Overview
Wanancry (2017) is a piece of malware described as ransomeware1 and a worm2 that, when introduced to an unpatched Windows machine, would encrypt the files and require a ransom payment of Bitcoin. Paying this fee would allegedly decrypt the files and free the infected machine.
How were devices infected?
Devices were infected using an exploit called EternalBlue. This exploit used a vulnerability in Windows SMB (Server Message Block)3 that allowed a remote code execution from any unpatched devices with SMBv1 enabled. Microsoft patched this vulnerability two months prior, which would have protected all vulnerable devices. Many users and organizations do not update operating systems regularly; this allowed WannaCry to spread even with the patch out.
What did WannaCry Do?
The TLDR of WannaCry (less technical)
When a device was infected with WannaCry, most files would be encrypted. This includes .docx, .gif, .png, .jpeg, .jpg, .vmdk, .mp3, .class, .zip, .backup, .sqlitedb, and many more important file extensions4. A message would then pop up demanding the payment of $300 in bitcoin to a given wallet address ($600 after 3 days). After 7 days the files would become unrecoverable.
Wanna Decrypt0r
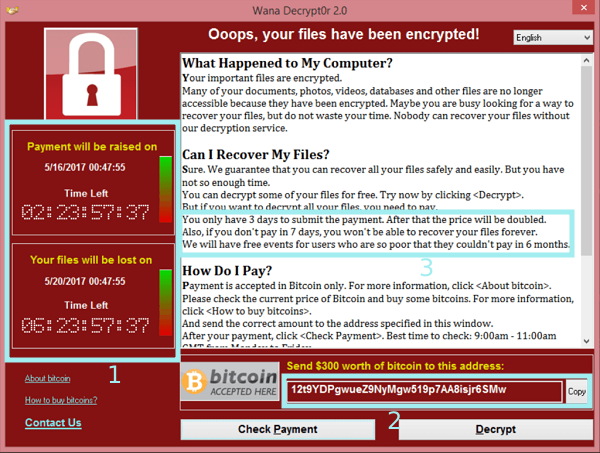
- 1 – Two timers indicating the time that the price will be raised (3 days) and the time until all files will be unrecoverable (7 days)
- 2 – The bitcoin wallet for users to (allegedly) decrypt files
- 3 – Paragraph stating the timeframes for payment
The Kill-switch
WannaCry would reach out to the domain “http://www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com,” and if the connection was not successful, the malware would continue infecting the machine. Once this piece of code was found, MalwareTech registered the domain. Using this newly registered site, which only cost $10.69, this strain of WannaCry was stopped in its tracks. Though new infections were prevented, those that had already taken place were still left to be dealt with.
There is no apparent reason why this was contained within the malware. The leading theory is that it is an intentional kill-switch that the creator(s) of WannaCry could use to stop the worm at any time.
Ransomware Mitigation
One of the best ways to protect oneself from ransomware is not to download any files from untrusted sources, click on emails from unknown senders (always check the domain), and keep software up to date. Updating software would have protected many from the rampage of WannaCry as the EternalBlue vulnerability was patched in March of 2017 and WannaCry began in May of 2017.
Keeping up-to-date backups is also a great way to fix a device if it happens to be infected. Paying the ransom has no guarantee of freeing a machine, but the malware will be removed if a device can be restored to a previous state before it was infected.
Extra
Ransomware –
Ransomware is a strain of malware that blocks a users access from files or an entire device with the promise that if a price is payed, access would be restored.
Worm –
A worm is a malware type that replicates itself from device to device without the help of a user.
SMB –
Server Message Block is a protocol created by Microsoft that is used for shared access to files and devices (printers) across a network.
File Extension List –
| .123 | .3dm | .3ds | .3g2 | .3gp | .602 | .7z | .ARC | .PAQ | .accdb |
| .aes | .ai | .asc | .asf | .asm | .asp | .avi | .backup | .bak | .bat |
| .bmp | .brd | .bz2 | .c | .cgm | .class | .cmd | .cpp | .crt | .cs |
| .csr | .csv | .db | .dbf | .dch | .der | .dif | .dip | .djvu | .doc |
| .docb | .docm | docx | .dot | .dotm | .dotx | .dwg | .edb | .eml | .fla |
| .flv | .frm | .gif | .gpg | .gz | .h | .hwp | .ibd | .iso | .jar |
| .java | .jpeg | .jpg | .js | .jsp | .key | .lay | .lay6 | .ldf | .m3u |
| .m4u | .max | .mdb | .mdf | .mid | .mkv | .mml | .mov | .mp3 | .mp4 |
| .mpeg | .mpg | .msg | .myd | .myi | .nef | .odb | .odg | .odp | .ods |
| .odt | .otp | .ots | .ott | .p12 | .pas | .pem | .pfx | .php | |
| .pl | .png | .pot | .potm | .potx | .ppam | .pps | .ppsm | .ppsx | .ppt |
| .pptm | .pptx | .ps1 | .psd | .pst | .rar | .raw | .rb | .rtf | .sch |
| .sh | .sldm | .sldx | .slk | .sln | .snt | .sql | .sqlite3 | .sqlitedb | .stc |
| .std | .sti | .stw | .suo | .svg | .swf | .sxc | .sxd | .sxi | .sxm |
| .sxw | .tar | .tbk | .tgz | .tif | .tiff | .txt | .uop | .uot | .vb |
| .vbs | .vcd | .vdi | .vmdk | .vmx | .vob | .vsd | .vsdx | .wav | .wb2 |
| .wk1 | .wks | .wma | .wmv | .xlc | .xlm | .xls | .xlsb | .xlsm | .xlsx |
| .xlt | .xltm | .xltx | .xlw | .zip |
